The malware in question is “Doki,” known as part of a group of threat actors many years ago. The primary purpose of this malware was to attack specific web servers in the hope of mining crypto-currency.
The threat actor is termed as Ngrok because of the privacy invader inclined towards using the service of Ngrok- a tool that makes your website go online. The malware used the service for hosting C&C (Command and Control) servers and had been functional since late 2018.
Analysts at Intezer Labs have come forth with the conclusion that hackers attacked the Docker installation program, and ultimately left the API’s management entirely insecure and exposed.
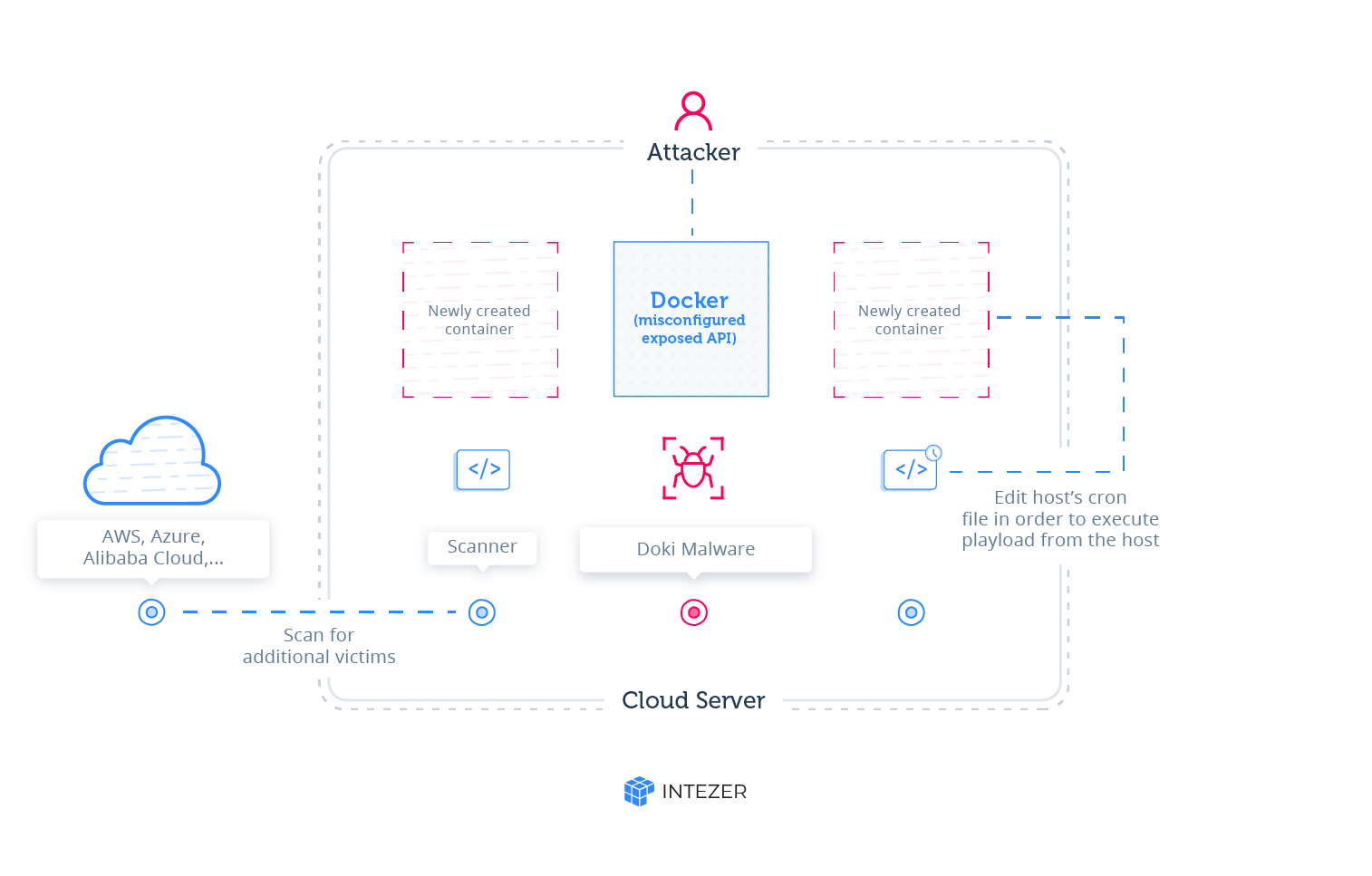
The Docker API was then manipulated to install a series of servers within a random company’s infrastructure. The version running with the servers was Alpine Linux and had been affected by Doki and other cryptocurrency mining malware. Doki functions by providing control to hackers in running and maintaining their freshly invaded Alpine Linux based servers, according to researchers. The malware certifies that the mining operation is going smoothly.
It’s quite interesting that the way Doki works might seem basic, but in truth, it offers a dynamic, unrealized role, as Intezer has affirmed. The significant difference between Doki and other backdoor trojans is that Doki uses a dynamic algorithm, otherwise termed as a DGA (domain generation algorithm). Using the Dogecoin API, it regulates C&C addresses.
Usually, what happens is malware form a connection to raw URLs, which is predetermined in their source code. Doki does not seem to work that way.
For convenience, the whole process has been described below by the brains at Intezer Labs themselves.
- Query dogechain.info API, a Dogecoin cryptocurrency block explorer, for the value that was sent out (spent) from a hardcoded wallet address that is controlled by the attacker. The format of the query is: https://dogechain.info/api/v1/address/sent/{address}
- Perform SHA256 on the value returned under “sent”
- Save the first 12 characters from the hex-string representation of the SHA256 value, to be used as the subdomain.
- Construct the full address by appending the subdomain to ddns.net. An example domain would be: 6d77335c4f23[.]ddns[.]net
The steps you’ve read mean that the Ngrok squad can easily replace the server where Doki gets its command list from. They would only have to make a transaction from the inside of the Dogecoin wallet that’s under their control.
If there’s a report developing from the Doki C&C URL, DynDNS will proceed to shut it down, but all in vain. The Ngrok hackers would just have to repeat the process of making another transaction, setting the value of the subdomain, make an all-new DynDNS account, and lastly, get the subdomain itself.
The process is truly cunning and seems thoroughly thought through. To completely take down Ngrok’s hacker squad, law enforcement agencies would have to access their Dogecoin wallet. Now that is virtually impossible without the wallet’s cryptographic key.
Also, malware is a ghost. Recent reports confirm that Doki has existed since January of 2020. Intezer further observes that the malware did not appear on any of the VirusTotal Linux scanning engines.
Given the fact that Doki is the latest threat to the digital world, the real danger problem is the consistent endangering of Docker servers. They have the target of these cryptocurrency mining hackers, along with several malware engineers.
Over the last few weeks, a multitude of reports from Palo Alto Networks, Aqua, and including one from Trend Micro came in that described the installation of DDoS malware in Docker servers. The summary of it is, Docker is severely targeted currently, and companies that feature the use of this software need to be careful that the interface’s API isn’t left bare online.
Intezer Labs say that the Ngrok is very much on the offensive right now, and take as little as 5 minutes to get their malware running across any Docker server that goes online.